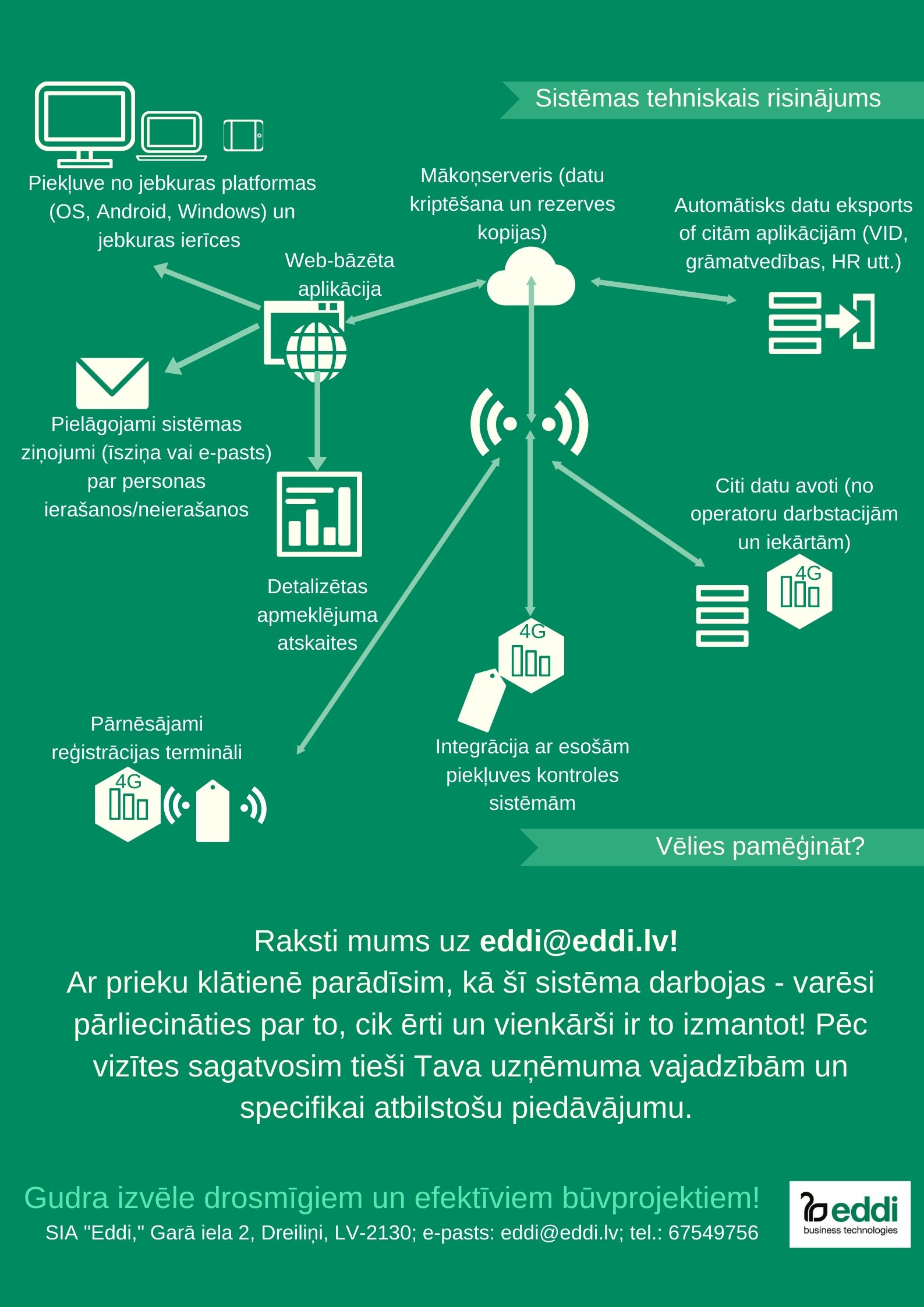
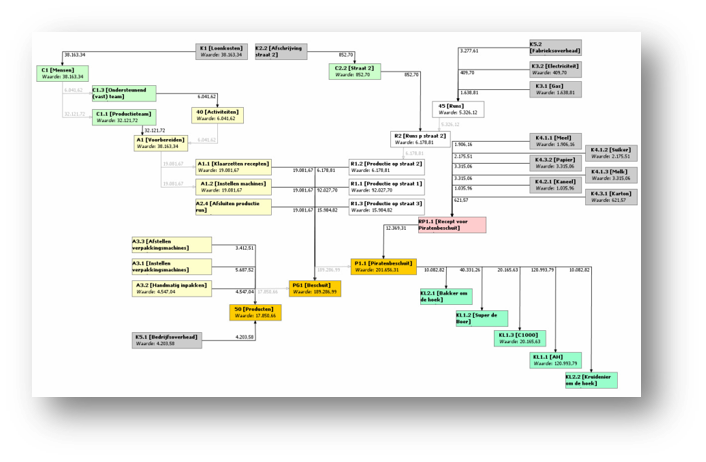
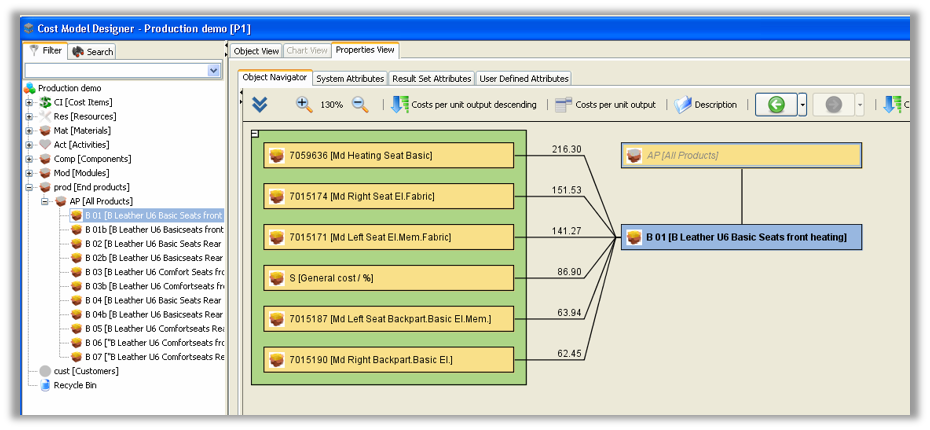
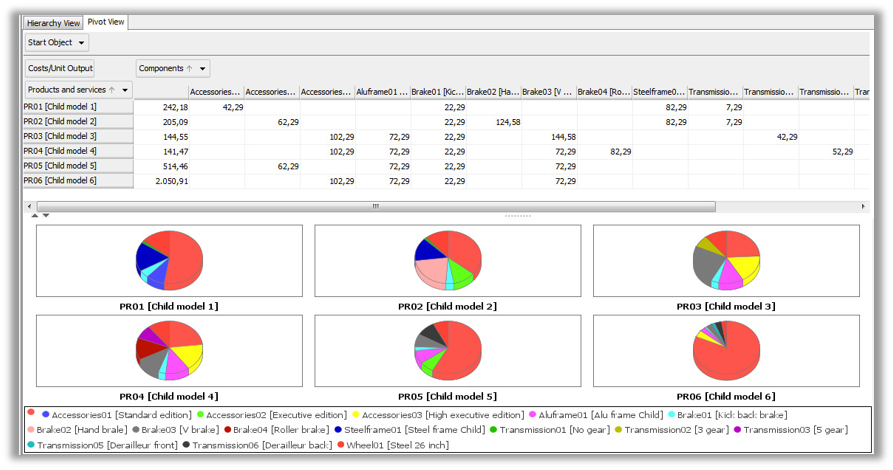
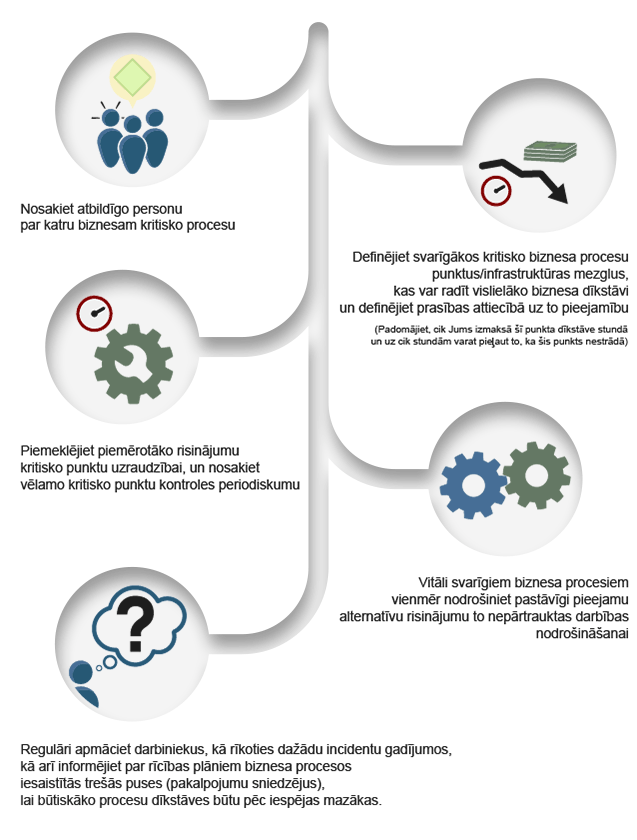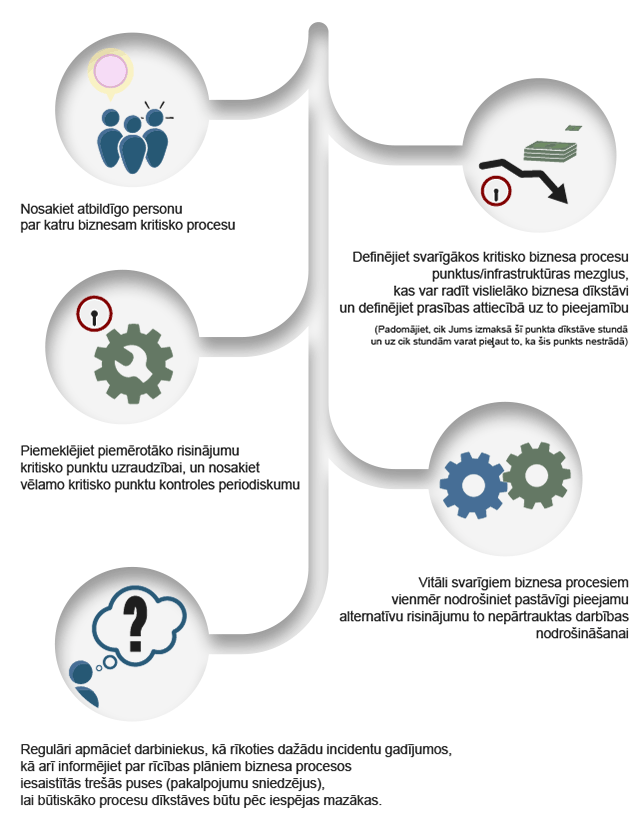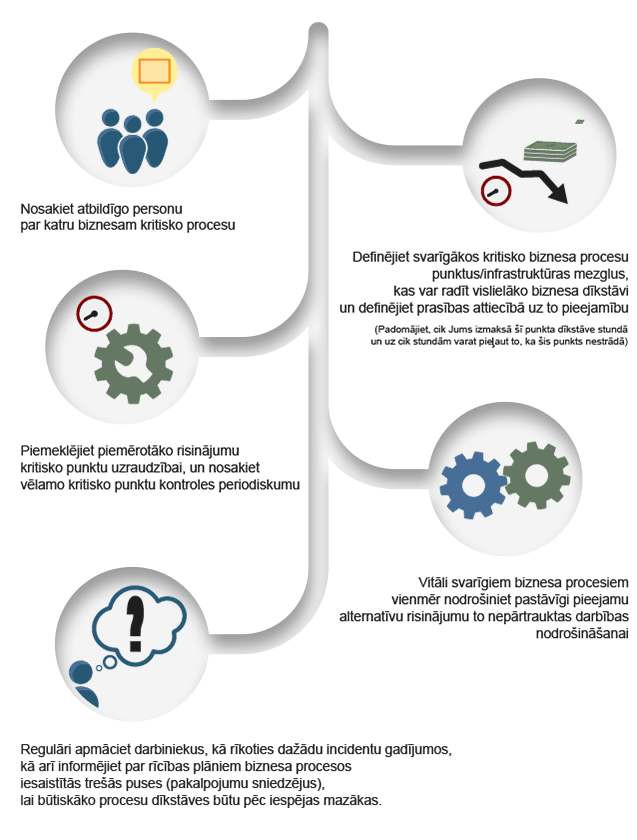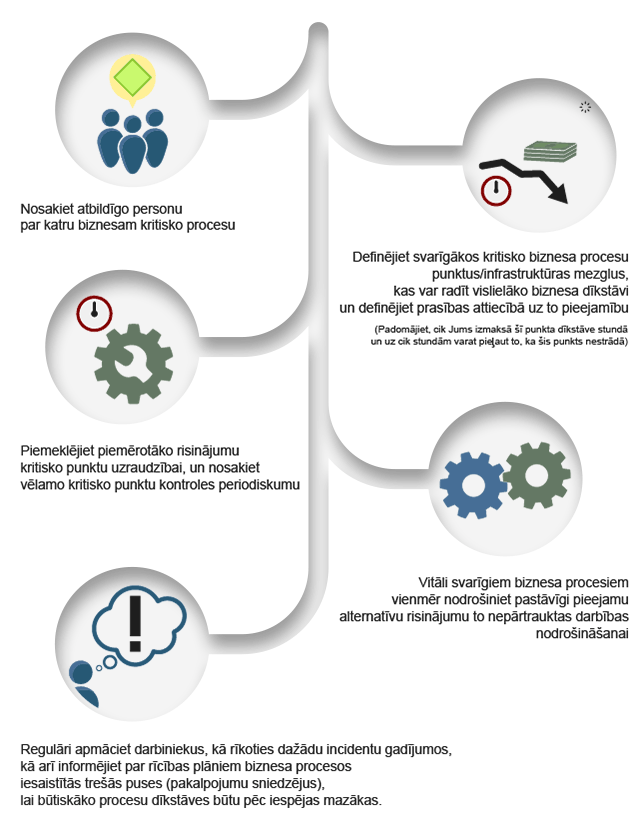
QPR ProcessAnalyzer ir rīks procesu analīzei un automatizētai biznesa procesu atklāšanai. Gudrs, ātri uzstādāms un ērti lietojams, tas pēta uzņēmuma operatīvos datus un nekavējoties atrod konkrētus veidus, kā uzlabot biznesa darbību.
Izmantojot no informācijas sistēmām ievāktus datus par darbinieku, iekārtu vai klientu veiktām aktivitātēm, īsā laikā iespējams iegūt:
- procesu atspoguļojumu;
- aktivitātes laikā;
- procesa soļu izmaksas;
- procesa variācijas;
- procesa neatbilstības gadījumus;
- cēloņu-seku analīzi;
- datu grupēšana, filtrēšana.
Laika veltīšana biznesa darbību procesu izpētei, ir nepieciešama, neatkarīgi no tā, kā veicas Jūsu uzņēmumam. Kad veicas labi, iespējams, atradīsiet veidus, kā padarīt procesus vēl efektīvākus. Ja neveicas tik labi, kā vajadzētu, pārliecināsieties, kurām darbībām ir javeic izmaiņas.